How to boost sales by improving your trust signals
If people do not trust your brand, your conversions will suffer no matter how persuasive your copy is.
5 things to do after a hack
Even if you try your utmost best, chances are hackers will find a way to hack your site. Following our WordPress security article, I’ll show you five things you should do right after you find your site to be hacked. Some of those things you should probably do before it even happens! 1. Understand what just […]
WordPress Security
WordPress security has always been food for thought. Even though most of the latest updates (including WordPress 4.5.2) deal with WordPress security issues, there is still a lot that can be done to improve that security, even by the less tech-savvy of us. In this article, I’d like to enumerate a number of suggestions on how to improve […]
No More Deceptive Download Buttons
(Cross-posted from the Google Security Blog.)
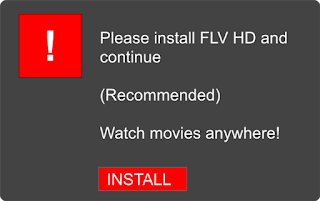
In November, we announced that Safe Browsing would protect you from social engineering attacks – deceptive tactics that try to trick you into doing something dangerous, like installing unwanted software or revealing your personal information (for example, passwords, phone numbers, or credit cards). You may have encountered social engineering in a deceptive download button, or an image ad that falsely claims your system is out of date. Today, we’re expanding Safe Browsing protection to protect you from such deceptive embedded content, like social engineering ads.
Consistent with the social engineering policy we announced in November, embedded content (like ads) on a web page will be considered social engineering when they either:
- Pretend to act, or look and feel, like a trusted entity — like your own device or browser, or the website itself.
- Try to trick you into doing something you’d only do for a trusted entity — like sharing a password or calling tech support.
Posted by Lucas Ballard, Safe Browsing Team
Managing a growing blog: technical SEO
As a blog starts growing, you’ll need to do more things to keep the technical aspects of your SEO covered. The first thing you should do, whether your blog is big or small, is installing our Yoast SEO plugin. That pretty much covers everything concerning technical SEO. We made it that simple. But, as your blog or website […]
Indexing HTTPS pages by default
As a natural continuation of this, today we’d like to announce that we’re adjusting our indexing system to look for more HTTPS pages. Specifically, we’ll start crawling HTTPS equivalents of HTTP pages, even when the former are not linked to from any page. When two URLs from the same domain appear to have the same content but are served over different protocol schemes, we’ll typically choose to index the HTTPS URL if:
- It doesn’t contain insecure dependencies.
- It isn’t blocked from crawling by robots.txt.
- It doesn’t redirect users to or through an insecure HTTP page.
- It doesn’t have a rel=”canonical” link to the HTTP page.
- It doesn’t contain a noindex robots meta tag.
- It doesn’t have on-host outlinks to HTTP URLs.
- The sitemaps lists the HTTPS URL, or doesn’t list the HTTP version of the URL
- The server has a valid TLS certificate.
Although our systems prefer the HTTPS version by default, you can also make this clearer for other search engines by redirecting your HTTP site to your HTTPS version and by implementing the HSTS header on your server.
We’re excited about taking another step forward in making the web more secure. By showing users HTTPS pages in our search results, we’re hoping to decrease the risk for users to browse a website over an insecure connection and making themselves vulnerable to content injection attacks. As usual, if you have any questions or comments, please let us know in the comments section below or in our webmaster help forums.
Posted by Zineb Ait Bahajji, WTA, and the Google Security and Indexing teams
Safe Browsing and Google Analytics: Keeping More Users Safe, Together
The following was originally posted on the Google Online Security Blog.
If you run a web site, you may already be familiar with Google Webmaster Tools and how it lets you know if Safe Browsing finds something problematic on your site. For example, we’ll notify you if your site is delivering malware, which is usually a sign that it’s been hacked. We’re extending our Safe Browsing protections to automatically display notifications to all Google Analytics users via familiar Google Analytics Notifications.
Google Safe Browsing has been protecting people across the Internet for over eight years and we’re always looking for ways to extend that protection even further. Notifications like these help webmasters like you act quickly to respond to any issues. Fast response helps keep your site—and your visitors—safe.
Posted by: Stephan Somogyi, Product Manager, Security and Privacy
WordPress security and Sucuri
When comparing WordPress to other website management platforms, people that favor other platforms tend to mock WordPress’ security. With the huge user base WordPress has, it’s not unlikely that hackers target WordPress websites. But that for sure doesn’t mean that WordPress is insecure per se! Actually, there is a lot that can be done to make it even more…
This post first appeared on Yoast. Whoopity Doo!
#NoHacked: a global campaign to spread hacking awareness
Webmaster level: All
This June, we introduced a weeklong social campaign called #NoHacked. The goals for #NoHacked are to bring awareness to hacking attacks and offer tips on how to keep your sites safe from hackers.
We held the campaign in 11 languages on multiple channels including Google+, Twitter and Weibo. About 1 million people viewed our tips and hundreds of users used the hashtag #NoHacked to spread awareness and to share their own tips. Check them out below!
Posts we shared during the campaign:
 https://plus.google.com/+GoogleWebmasters/posts/1BzXjgJMGFU
https://plus.google.com/+GoogleWebmasters/posts/1BzXjgJMGFU
 https://plus.google.com/+GoogleWebmasters/posts/TMhfwQG3p8P
https://plus.google.com/+GoogleWebmasters/posts/TMhfwQG3p8P
 https://plus.google.com/+GoogleWebmasters/posts/AcUS4WhF6LL
https://plus.google.com/+GoogleWebmasters/posts/AcUS4WhF6LL
Some of the many tips shared by users across the globe:
- Pablo Silvio Esquivel from Brazil recommends users not to use pirated software (source)
- Rens Blom from the Netherlands suggests using different passwords for your accounts, changing them regularly, and using an extra layer of security such as two-step authentication (source)
- Дмитрий Комягин from Russia says to regularly monitor traffic sources, search queries and landing pages, and to look out for spikes in traffic (source)
- 工務店コンサルタント from Japan advises everyone to choose a good hosting company that’s knowledgeable in hacking issues and to set email forwarding in Webmaster Tools (source)
- Kamil Guzdek from Poland advocates changing the default table prefix in wp-config to a custom one when installing a new WordPress to lower the risk of the database from being hacked (source)
Hacking is still a surprisingly common issue around the world so we highly encourage all webmasters to follow these useful tips. Feel free to continue using the hashtag #NoHacked to share your own tips or experiences around hacking prevention and awareness. Thanks for supporting the #NoHacked campaign!
And in the unfortunate event that your site gets hacked, we’ll help you toward a speedy and thorough recovery:
Posted by your friendly #NoHacked helpers
HTTPS as a ranking signal
Webmaster level: all
Security is a top priority for Google. We invest a lot in making sure that our services use industry-leading security, like strong HTTPS encryption by default. That means that people using Search, Gmail and Google Drive, for example, automatically have a secure connection to Google.
Beyond our own stuff, we’re also working to make the Internet safer more broadly. A big part of that is making sure that websites people access from Google are secure. For instance, we have created resources to help webmasters prevent and fix security breaches on their sites.
We want to go even further. At Google I/O a few months ago, we called for “HTTPS everywhere” on the web.
We’ve also seen more and more webmasters adopting HTTPS (also known as HTTP over TLS, or Transport Layer Security), on their website, which is encouraging.
For these reasons, over the past few months we’ve been running tests taking into account whether sites use secure, encrypted connections as a signal in our search ranking algorithms. We’ve seen positive results, so we’re starting to use HTTPS as a ranking signal. For now it’s only a very lightweight signal — affecting fewer than 1% of global queries, and carrying less weight than other signals such as high-quality content — while we give webmasters time to switch to HTTPS. But over time, we may decide to strengthen it, because we’d like to encourage all website owners to switch from HTTP to HTTPS to keep everyone safe on the web.
In the coming weeks, we’ll publish detailed best practices (we’ll add a link to it from here) to make TLS adoption easier, and to avoid common mistakes. Here are some basic tips to get started:
- Decide the kind of certificate you need: single, multi-domain, or wildcard certificate
- Use 2048-bit key certificates
- Use relative URLs for resources that reside on the same secure domain
- Use protocol relative URLs for all other domains
- Check out our Site move article for more guidelines on how to change your website’s address
- Don’t block your HTTPS site from crawling using robots.txt
- Allow indexing of your pages by search engines where possible. Avoid the noindex robots meta tag.
If your website is already serving on HTTPS, you can test its security level and configuration with the Qualys Lab tool. If you are concerned about TLS and your site’s performance, have a look at Is TLS fast yet?. And of course, if you have any questions or concerns, please feel free to post in our Webmaster Help Forums.
We hope to see more websites using HTTPS in the future. Let’s all make the web more secure!
Posted by Zineb Ait Bahajji and Gary Illyes, Webmaster Trends Analysts
Regular security audits: taking our responsibility
Today, we’re announcing that we have partnered with Sucuri, in the interest of pro-actively securing our plugins. As our plugins run on more and more sites, we have a responsibility towards our users and the web at large to make sure that we do our utmost to make sure our code doesn’t make them vulnerable.* We’ve…
This post first appeared on Yoast. Whoopity Doo!
10 Surprising Facts About “Keyword (Not Provided)” For Paid Search
Earlier this week, everyone went bananas over a rumor that paid search query data was disappearing and that third party tools providers would be slammed. In my article, I’ll clarify fact from fiction. Here are 10 things you need to know about the Keyword (Not Provided) for paid search issue: 1. Can…
Please visit Search Engine Land for the full article.
Not Provided Comes To Paid Search: What Will The Impact Be?
If you’re reading this, you probably already know that Google is making changes that will bring the much-maligned “(not provided)” to paid search. The AdWords world has been abuzz about the change for the past few days. The gist of the development is that when people using secure…
Please visit Search Engine Land for the full article.
Should we move to an all HTTPS web?
There was a bit of tweeting in the SEO community today because Bing introduced an HTTPS version of their site and people thought that would mean they’d lose their keyword data. That’s not true, if you take the right precautions. I thought I’d write a bit of an intro in how all this works so…
This post first appeared on Yoast. Whoopity Doo!
Search Engines Ixquick & StartPage Double Up On Security Measures With 2 New Encryption Standards
On the heels of the US PRISM scandal, private search engines Ixquick and its partner site StartPage are leveraging new encryption methods that offer higher levels of security beyond the standard SSL encryption. With a combined four millions searches da…



 https://plus.google.com/+GoogleWebmasters/posts/DUTpSGmkBUP
https://plus.google.com/+GoogleWebmasters/posts/DUTpSGmkBUP https://plus.google.com/+GoogleWebmasters/posts/UjZRbySM5gM
https://plus.google.com/+GoogleWebmasters/posts/UjZRbySM5gM